Penetration testing ethics
into security practice, there is little literature devoted to the ethical pressures associated with penetration testing. This paper presents several ethical dilemmas .






24 Jan Penetration testing, or ethical hacking, is an in-demand skill for evaluating an organization's defenses. Here's what it entails and tips for.


Ethical Hacking vs. Penetration Testing

My name Brianne Age: 19. But today, she's ready to have dozens of guys jizz for her, and then drink their collective loads in shot glasses.Hot and depraved bitch in bed and luxurious lady for a party, events or dinner date !I am a passionat, outgoing and sensual lady with style, who knows how to meet a mans highest desires plessioures and fantasies,



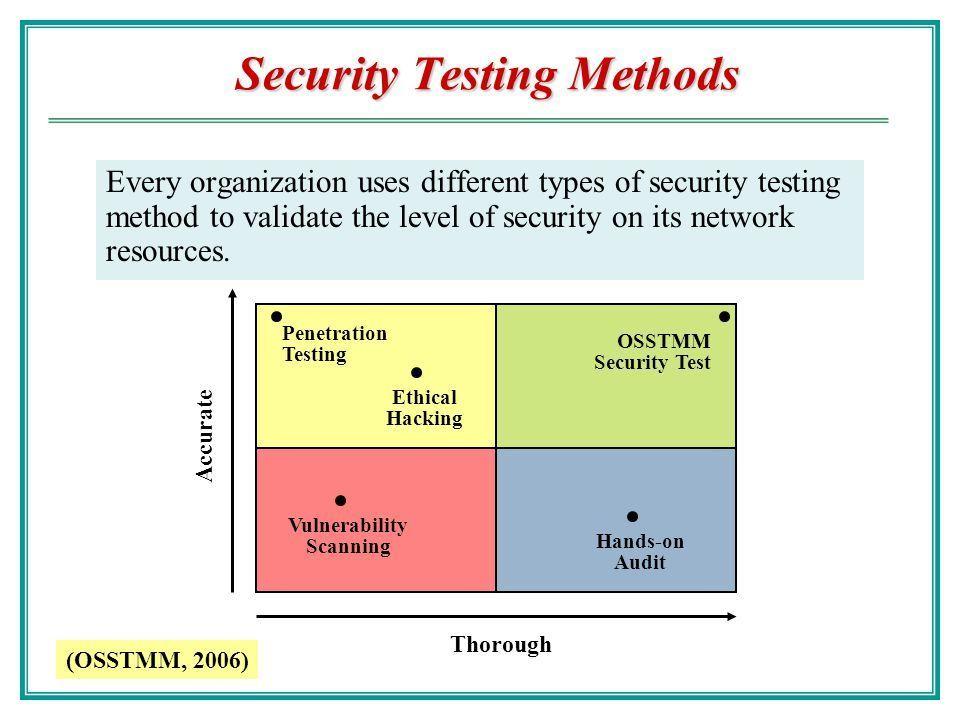

Ethics of penetration testing
Ethics of penetration testing. April Laptop in chains Steven Furnell and Maria Papadaki from the Centre for Security, Communications and Network.





Hi, i am Lizzie Age: 18. Professionale nei massaggi rilassanti e completi in ambiente confortevole e riservatoI am gfe, very open-minded genuine,sophisticated and i can promise you i will make your desires a dream.
Description:To have a better grasp of the controversy called gray hat hackers, imagine how you would feel if an unknown person s compromises your computer system, without obtaining first permission from you, out of a desire to show you what you need to do to fix the backdoors he has taken advantage of. Provide service in your areas of competence, being honest and forthright about any limitations of your experience and education. This not only applies to production software, but to security controls and monitoring tools as well. So, while there might be a clearly intended professional interpretation, it is easy to see how the term could be misrepresented to justify cyber vigilantism and other unsanctioned activities, with the perpetrators claiming they were operating with ethical intent. Penetration Testing A narrow term which focuses on performing cyber security assessment on IT systems A comprehensive term in which penetration testing is only one feature A tester needs to have a good knowledge and skills only in the specific area for which he conducts pen testing An ethical hacker needs to possess a comprehensive knowledge of various programming and hardware techniques Anyone who is familiar with penetration testing can perform pen tests Usually is required an obligatory certification of ethical hacking Access is required only to those systems on which the pen testing will be conducted Access is required to a wide range of computer systems throughout an IT infrastructure Interested in receiving an online hacker certification? Generally speaking, organizations conduct pen tests to strengthen their corporate defense systems comprising all computer systems and their adjoining infrastructure. Never knowingly use software or process that is obtained or retained either illegally or unethically.


































User Comments 1
Post a comment
Comment: